Cybersecurity leaders hold a pivotal responsibility in managing the intricate challenges of digital risks while safeguarding their organizations with strong security measures. As cyber threats become more advanced and widespread, these individuals are charged with more than just crafting and executing cybersecurity strategies—they are also key to nurturing a culture of security awareness (not only phishing protection) across the entire organization.
Their responsibilities encompass identifying gaps in cybersecurity measures, aligning these strategies with business objectives, and addressing emerging risks effectively.
Pushing security initiatives forward is essential—not only to safeguard data, but also to maintain business continuity and uphold integrity. In this posting, we’ll dive into strategies that cybersecurity leaders can use to build trust, craft engaging narratives, and align security efforts with broader business goals. The aim? To cultivate a security-focused culture that truly resonates throughout the entire organization.
Understanding the Landscape
Cybersecurity has evolved beyond being merely a technical concern—it's now a critical business priority. With the increasing prevalence of ransomware, phishing schemes, and cyber espionage by nation-states, the risks have never been greater. Strong leadership in cybersecurity demands a forward-thinking approach, integrating security measures seamlessly with the broader objectives of the organization.
However, this vision often needs to be implemented without the luxury of formal authority, making influence a critical skill for cybersecurity leaders.
In the world of cybersecurity, the idea of authority has undergone a notable transformation. In the past, leadership was typically tied to official titles and rigid hierarchies. But in today’s highly connected digital environment, true leadership goes far beyond these traditional frameworks. Cybersecurity leaders are increasingly recognized for their ability to influence and drive change without relying solely on formal authority.
The Role of Influence Over Authority
Cybersecurity leadership is not confined to those in executive roles; it includes individuals at various levels who possess the skills to lead through influence rather than title. This “informal leadership” model emphasizes the importance of relationships, trust, and effective communication. Leaders who can inspire their teams and foster collaboration are often more successful than those who merely rely on their positional power.
So, the question remains open:
How to influence and drive change without relying solely on formal authority?Let’s try to get into some possible strategies in more detail:
Empowering Others
One of the key traits of effective cybersecurity leaders is their ability to empower others within the organization. By encouraging team members to take initiative and promoting a culture of shared responsibility, leaders can drive meaningful change even in the absence of formal authority. This empowerment is crucial in a field like cybersecurity, where the collective effort of all employees plays a pivotal role in safeguarding digital assets.
Fostering a Cybersecurity Culture
A significant aspect of cybersecurity leadership is the cultivation of a security-conscious culture. The effectiveness of advanced security technologies can be undermined if employees are not educated about their roles in cybersecurity.
For instance, phishing scams often exploit human behavior rather than technological flaws, highlighting the importance of awareness and training initiatives led by cybersecurity leaders. By championing these efforts, leaders can foster a culture where every individual understands their responsibility in safeguarding digital assets.
Overall, leaders must adopt strategies that promote desired behaviors while aligning with the overall strategic priorities of the organization. Even in the absence of formal authority, leaders can drive cultural change by demonstrating credibility and presenting compelling business cases that resonate with stakeholders.
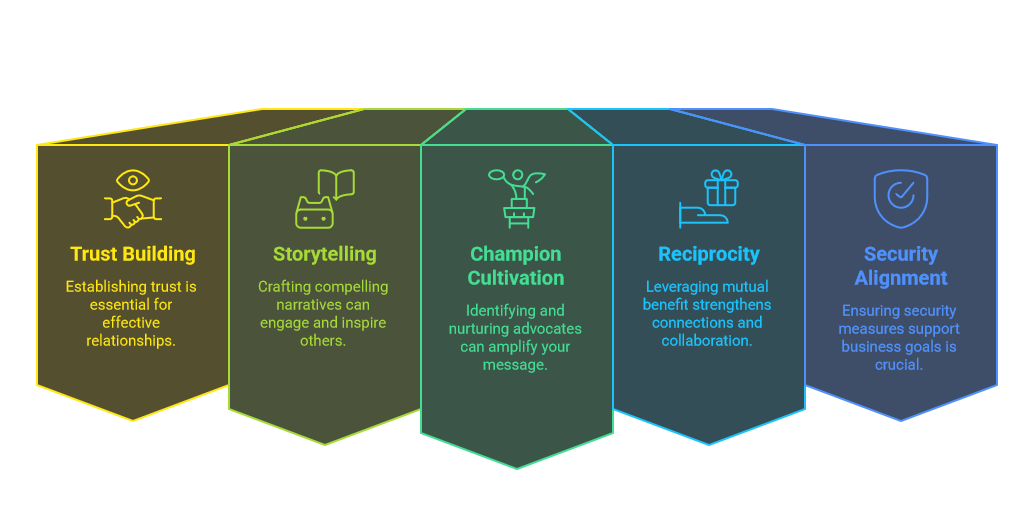
Building Trust and Telling Compelling Stories
Trust is the foundation upon which all influence is built. Cybersecurity leaders must foster an environment where team members feel comfortable sharing concerns and offering feedback. This not only helps in identifying potential security risks early, but also builds a culture of transparency and collaboration. Telling compelling stories about the impact of cybersecurity on business outcomes can also galvanize support across departments. By framing security initiatives in terms of business benefits rather than technical jargon, leaders can create a shared vision that resonates with stakeholders.
Cultivating Champions and Leveraging Reciprocity
Influencing without authority often requires identifying and cultivating champions within the organization. These champions can help amplify the message and build support for security initiatives. Additionally, leveraging reciprocity—where favors are exchanged in a mutually beneficial manner—can create a network of allies who are invested in the success of cybersecurity efforts. This approach not only fosters cooperation but also ensures that security is seen as a collaborative effort rather than a solitary function.
Aligning Security with Business Outcomes
Perhaps the most effective strategy for influencing without authority is to align security initiatives with business outcomes. By demonstrating how robust cybersecurity practices can enhance operational efficiency, protect revenue streams, and improve customer trust, leaders can make a compelling case for investment in security. This alignment requires a in-depth understanding of the organization's strategic goals and the ability to communicate security benefits in business terms.
Case Studies
The effectiveness of cybersecurity leadership often hinges on the ability to influence and drive change without relying on formal authority. Let’s highlight some case studies that illustrate how leaders in the cybersecurity domain can implement successful strategies through influence, collaboration, and innovative thinking.
Cybersecurity Strategies from Industry Giants
In a collection of case studies featuring major companies like PayPal, Chevron, and IBM, the narratives detail their responses to significant cybersecurity challenges. These cases reveal the practical applications of cybersecurity strategies that enhance business resilience and security. For example, initiatives such as encryption overhauls and advanced threat intelligence platforms demonstrate how these organizations adapted their cybersecurity posture to meet evolving threats, emphasizing the necessity of strategic thinking and collaboration across departments to achieve comprehensive security measures.
Cisco's Predictive Analytics Approach
A specific case study involves Cisco, which faced challenges in protecting its vast network infrastructure from sophisticated cyber threats. The company implemented predictive analytics to enhance its network security, aiming to identify potential breaches before they occurred. This proactive approach required not just technological solutions, but also the influence of cybersecurity leaders to advocate for and implement these measures within the organization, showcasing the importance of leadership without formal authority in driving critical security initiatives.
Call to Action
Clear communication is absolutely essential. For cybersecurity leaders, connecting with their audience through thoughtful and empathetic dialogue can make all the difference in overcoming pushback. Taking the time to genuinely listen to concerns and objections builds trust and provides meaningful insights that can shape their strategy and close any gaps in understanding. By focusing on shared objectives and fostering agreement, it's possible to ease doubts and encourage teamwork.
At its core, influencing without direct authority isn’t about trying to control or manipulate—it’s about cultivating a collective vision for a safer and more secure future.
By building:
trust,
telling compelling stories,
cultivating champions,
leveraging reciprocity,
and aligning security with business outcomes,
cybersecurity leaders can drive significant change even without formal authority.
As we navigate the complex threat landscape of the digital age, it's crucial for leaders to embrace these strategies and foster a culture of security that is proactive, collaborative, and deeply integrated into the fabric of the organization.
Let's join forces to make cybersecurity a top business priority and strengthen our organizations against ever-changing threats.
I'd love to hear your stories and strategies for driving change within your organization—feel free to share your thoughts in the comments so we can keep this conversation going.