Mental Models for Security Risk Management
Key Frameworks and Applications in Modern Cybersecurity
In cybersecurity, where threats are as dynamic as the technologies they exploit, relying solely on checklists and reactive measures is akin to navigating a labyrinth blindfolded. To truly master security risk management, professionals need more than tools and procedures – they need some solid mental models. These frameworks, cognitive shortcuts, and conceptual lenses provide structured ways to understand complex systems, anticipate threats, and make informed decisions, transforming chaotic data into actionable insights.
Before we dive into the brain-tickling world of mental models for security risk management, let me lay a quick disclaimer on the table:
I’m definitely not a psychologist. But that doesn’t stop me from waving my pom-poms for the human factor in cybersecurity. After all, it’s us flawed, lovable humans who click the links, open the emails, and—every once in a while—fall for a well-crafted phishing scam like a raccoon spotting a shiny object.
In this blog post, we’ll explore how resetting some of our mental gears—like reframing risk, using scenario planning, or trusting our gut instincts—can lock the digital baddies out. Based on my research and interviews (with real professionals on this topic), I’ll offer a few approaches you can weave into your day-to-day operations, mixing a dash of common sense with a sprinkle of strategic thinking. Most importantly, we’ll learn that embracing our human quirks can actually reduce the chance of data breaches and sleepless nights.
Ready to dive in? Let’s strap on our tin-foil hats and do some mental gymnastics to outsmart the cyber crooks!
Components of Security Risk Management
Before we jump on the psycho-train, let’s recap the main components of Risk Management first.
The foundation of effective security risk management lies in thorough risk assessments, which are typically divided into two main parts:
threat assessment
and vulnerability assessment.
The threat assessment identifies potential threats to the organization, while the vulnerability assessment evaluates the weaknesses that could be exploited by these threats.
Another essential element in security risk management is scenario-driven risk assessment, which emphasizes preparing for various potential incidents by analyzing past events and stakeholder responses. This involves focusing on key moments, such as crisis peaks and resolution phases, to shape perceptions and learning outcomes from security incidents. By training security teams, security leaders and decision makers to perform optimally during critical times and ensuring clear communication post-incident, organizations can significantly enhance their preparedness.
There are also some established frameworks that integrate mental models into structured approaches for managing cybersecurity risks, like:
NIST Cybersecurity Framework (CSF):
A widely adopted framework offering a structured approach to identify, protect, detect, respond to, and recover from cyber threats.
FAIR (Factor Analysis of Information Risk):
A quantitative model that assesses risk by analyzing the frequency and impact of potential threats.
ISO 31000:
Provides principles and guidelines for risk management across industries.
So I hope this recap sets a foundation to understand the approach and benefits of using mental models within the risk management.
Understanding Mental Models
Mental models for security risk management are cognitive frameworks that assist security professionals in understanding, assessing, and responding to various risks within organizational contexts. These models simplify complex security scenarios, enabling better decision-making and more effective risk mitigation strategies.
In cybersecurity, these models often draw from analogies or metaphors, such as comparing cyber risks to medical infections, criminal activities, or physical security breaches. These frameworks enable stakeholders to conceptualize abstract threats in more familiar terms, thereby improving communication and decision-making.
Practical Applications in Modern Cybersecurity
Security risk management requires strategic thinking to identify underexplored areas that could lead to cost reductions or risk minimization. Applying probabilistic and first principle thinking (by using mental models) allows security managers to break down complex problems into their fundamental elements, facilitating more effective decision-making.
Mental models are not just theoretical constructs; they have practical implications for addressing real-world challenges. Here some common strategies:
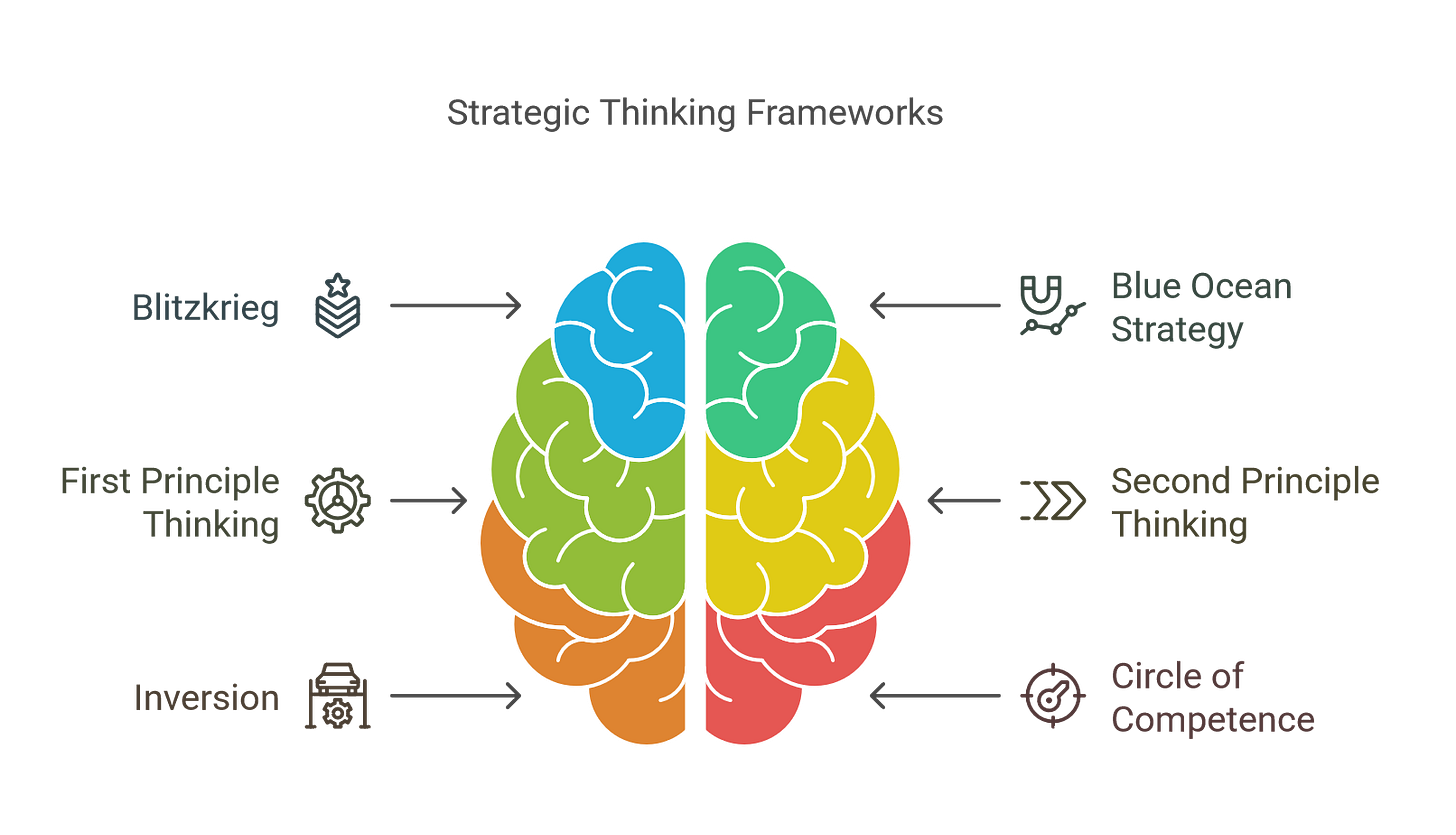
Blitzkrieg (Rapid Response)
Sounds weird in the context of cybersecurity - but true. Originating as a military strategy (you couldn't expect that), the Blitzkrieg approach focuses on:
rapid,
and decisive action against threats.
In security risk management, this model translates to swiftly mobilizing resources and executing emergency protocols to counteract breaches or incidents. The key is to manage critical moments during a security event effectively, shaping stakeholders' perceptions and learning outcomes through decisive action.
By following this approach, some organizations could swiftly detect anomalies and deploy countermeasures to significantly minimize damage, during the 2020 SolarWinds attack.
Blue Ocean Strategy
The Blue Ocean Strategy emphasizes the creation of new market spaces where competition is irrelevant. In security risk management, this can be a powerful lens. It encourages moving beyond the "red ocean" of traditional, competitive cybersecurity practices and creating new, uncontested market spaces or "blue oceans" where risk is minimized in innovative ways.
By thinking creatively and exploring uncharted territories, organizations can differentiate themselves and improve their security posture. Usually, this implies shifting the focus:
from reacting to threats
to proactively eliminating or mitigating entire classes of risks.
All this with the goal of creating a unique security postures that make organizations less attractive targets or fundamentally disrupt attack vectors. By adopting and adapting these models, practitioners can enhance their decision-making capabilities and contribute to more robust security practices within their organizations.
First Principle Thinking
First principle thinking involves breaking down complex problems into their fundamental components and reassembling them from the ground up. This model encourages security professionals to:
question assumptions
and explore innovative solutions
instead of relying on conventional practices. By focusing on the core principles underlying a security issue, practitioners can develop unique strategies tailored to specific challenges, thus enhancing overall security effectiveness.
Second Principle Thinking
Second principle thinking builds upon the insights of first principle thinking by considering the potential second-order effects of decisions. This model prompts security professionals to:
evaluate the long-term consequences of their actions,
ensuring that immediate solutions do not inadvertently create new vulnerabilities or risks.
It encourages a holistic view of security implications, promoting more sustainable practices within organizations.
Inversion
Inversion is a mental model that involves thinking about a problem from the opposite perspective. Instead of asking how to achieve success, security professionals might consider what actions could lead to failure.
By identifying potential pitfalls and vulnerabilities, this approach helps to mitigate risks before they materialize. This model fosters a proactive mindset, encouraging teams to anticipate threats and develop effective countermeasures.
Circle of Competence
The circle of competence model emphasizes the importance of understanding one's own strengths and weaknesses. Security professionals are encouraged to recognize the limits of their knowledge and expertise, which allows them to seek assistance or additional resources when necessary.
By operating within their circle of competence, security teams can make more informed decisions and avoid overextending themselves in areas outside their expertise.
Practical Applications in Modern Cybersecurity
Mental models are not just theoretical constructs; they have practical implications for addressing real-world challenges:
Application in Crisis Management
In the context of security incidents, managing the peak moments and resolution phases is crucial for shaping stakeholders' perceptions. By applying mental models during these critical times, security teams can:
enhance communication,
maintain clarity,
and ensure that responses are both effective and well-coordinated.
This proactive management approach contributes to improved learning outcomes post-incident, aiding in future preparedness and resilience.
Training and Implementation
To maximize the benefits of mental models in security risk management, organizations should prioritize training their teams on these frameworks. Structured workshops can cultivate critical thinking and promote a shared understanding among team members. Key components of this training include:
identifying relevant models,
facilitating collaborative learning,
applying real-world scenarios,
and encouraging continuous reflection on experiences and decisions.
By integrating these practices, security professionals can enhance their analytical skills and better prepare for the complexities of the security landscape.
Example:
During the 2020 SolarWinds attack, companies like Microsoft and FireEye quickly identified anomalies and responded decisively, demonstrating how a Blitzkrieg model can enhance resilience against sophisticated attacks. This approach requires well-trained teams, robust intelligence systems, and a high level of resource commitment.
Challenges and Limitations
Mental models, while instrumental in decision-making and problem-solving within security risk management, present several challenges and limitations that can hinder effective outcomes.
Cognitive Biases in Decision-Making
These biases can lead individuals and organizations to overlook vital information, resulting in misjudgments in risk assessment and decision-making.
Subjectivity of Impact Assessment
The cost associated with the loss of integrity, availability, or confidentiality of information often varies depending on the individual's or organization's context and perspective. This variability complicates the establishment of universal mental models, as different stakeholders may perceive risks and their implications different.
Overreliance on Simplified Frameworks
Relying too heavily on simplified mental models can lead to cognitive overload, decision fatigue, and a reduction in the quality of choices over time. Managers might streamline their decision processes through heuristics, but this can inadvertently obscure comprehensive analysis and critical thinking.
Difficulty in Testing Best Practices
Many security policies and best practices are based on anecdotal evidence and case studies rather than empirical testing. The challenge of rigorously testing these policies in live environments without exposing networks to unnecessary risks complicates the development of effective mental models.
Balancing Intuition and Data
As technology advances, the integration of AI and real-time data analytics into decision-making frameworks presents both opportunities and challenges. While data insights can support decision-making, they may also overwhelm managers if not appropriately balanced with intuitive judgment.
Looking Ahead
The evolving landscape of security risk management is significantly influenced by advancements in technology and the increasing complexity of threats. As organizations continue to adapt, several key trends are shaping the future of mental models in this field.
Integration of Predictive Analytics
The adoption of predictive analytics is poised to revolutionize decision-making processes in security risk management. By leveraging vast amounts of data (with AI-driven threat detection systems), organizations can forecast trends and anticipate potential threats with greater accuracy, enabling a proactive rather than reactive approach to risk management. This data-driven insight allows managers to refine their mental models, facilitating more informed decisions that transcend intuition and experiences.
Scenario Planning for Agility
Scenario planning will become increasingly vital as organizations seek to remain agile in a volatile business environment. By exploring multiple potential futures, decision-makers can better identify risks and opportunities, fostering resilience and strategic agility. This proactive mindset enhances crisis management and nurtures a culture of innovation, encouraging teams to think creatively about possible outcomes.
Emphasis on Human-Centric Approaches
As cybersecurity continues to be recognized as a primarily human problem, there is a growing need for mental models that prioritize human behavior over technology.
Effective security controls must be designed around human actions and decision-making processes, emphasizing training and cultural awareness as foundational elements in mitigating risks. This shift necessitates a reevaluation of existing mental models to integrate psychological principles that enhance understanding and responsiveness to security threats.
Development of Adaptable Frameworks
Future developments in mental models for security risk management will likely focus on creating adaptable frameworks that accommodate industry-specific challenges while integrating broader cognitive principles. Organizations can take advantage of this flexibility by utilizing mental models in a more effective manner, which helps align their decision-making processes with the specific complexities of their unique business environments.
Continuous Learning and Adaptation
Given the dynamic nature of information security threats, organizations will need to foster a culture of continuous learning and adaptation. Regular risk assessments and updates to mental models will be essential in keeping pace with emerging threats and technological advancements.
Encouraging proactive risk management and awareness among all employees will help cultivate resilience and preparedness as new challenges arise.
Let’s conclude…
To effectively implement mental models in security risk management:
Conduct regular training sessions to align team members' mental models with organizational goals.
Use quantitative frameworks like FAIR to translate abstract risks into measurable metrics.
Continuously reassess and adapt frameworks based on evolving threats and technological advancements.