Let’s face it
— the traditional Security Operations Center (SOC) can feel a lot like an endless game of whack-a-mole. An alert shows up? You deal with it. Another one? Same routine.
Sure, it keeps you busy, but does it truly make your organization secure? Probably not. Constantly chasing after the latest threat leaves little space for a proactive approach—and let’s be honest, the attackers always seem to be one step ahead. There’s a better solution, a smarter approach. It’s time to step off the reactive security treadmill and unlock the potential of an Intelligence-Led SOC.
Intel-Driven Vision
An Intelligence-Led and Threat-Informed Security Operations Center (SOC) is a proactive cybersecurity strategy that leverages threat intelligence to anticipate and mitigate threats. This proactive approach shifts the focus from reactive alert management to proactive threat hunting, guided by insights into adversary tactics, techniques, and procedures (TTPs). By understanding the threat landscape and potential attack vectors relevant to the organization, the SOC can prioritize alerts, improve detection and response capabilities, reduce dwell time, optimize resource allocation, and strengthen the overall security posture.
The result is a more resilient and agile security operation capable of anticipating and mitigating threats before they can impact the organization.
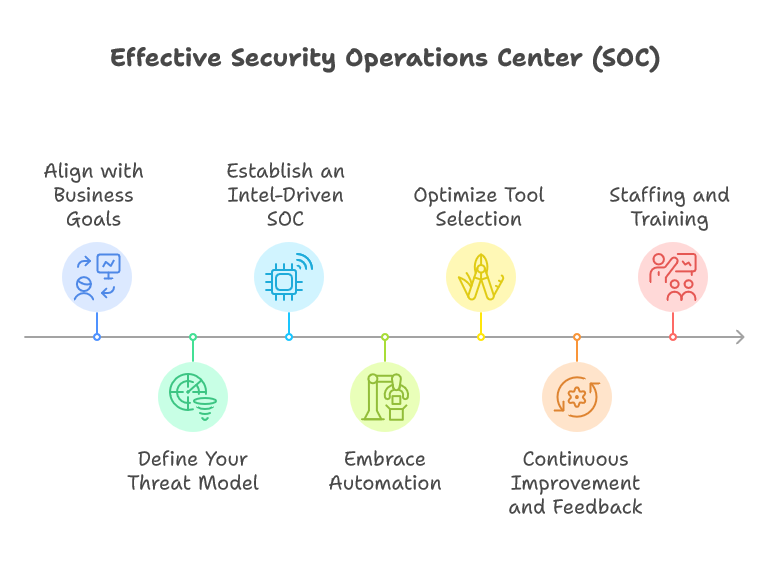
The framework for building an intelligence-led SOC encompasses several key steps:
align with Business Goals,
defining a threat model,
establishing intelligent SOC capabilities,
embracing automation,
optimizing tool selection,
fostering continuous improvement,
and investing in staffing and training.
Traditional SOC vs. Intelligence-Led
Before we dive into the idea of creating this proactive environment, let's take a step back and talk about some key differences between an Intelligence-Led SOC and a Traditional SOC.
They can be summarized as follows:
Operational Focus
Traditional SOC: Focuses primarily on monitoring and responding to security alerts based on predefined rules and known threats. It relies heavily on manual processes and human analysts to detect and respond to threats.
Intelligence-Led SOC: Emphasizes proactive threat detection and response by leveraging threat intelligence to anticipate potential threats. It integrates advanced technologies like AI and ML to enhance threat detection capabilities.
Threat Detection Approach
Traditional SOC: Typically uses rule-based systems to identify known threats. It may struggle with detecting unknown or advanced threats without specific rules in place.
Intelligence-Led SOC: Utilizes threat intelligence to identify both known and unknown threats. It analyzes adversary tactics, techniques, and procedures (TTPs) to stay ahead of evolving threats.
Technology Integration
Traditional SOC: Often relies on manual processes and traditional security tools like SIEM systems without extensive AI integration.
Intelligence-Led SOC: Heavily integrates AI and ML to automate processes, reduce false positives, and enhance threat prioritization.
Resource Utilization
Traditional SOC: Requires significant human resources and continuous training to keep up with evolving threats. It can be resource-intensive and costly.
Intelligence-Led SOC: Optimizes resource allocation by automating repetitive tasks, allowing analysts to focus on high-priority threats and strategic planning.
Proactivity vs. Reactivity
Traditional SOC: Tends to be more reactive, responding to threats after they have been detected.
Intelligence-Led SOC: Proactive approach, focusing on anticipating and preventing threats before they occur.
Data Analysis and Integration
Traditional SOC: May not fully leverage external threat intelligence or integrate diverse data sources effectively.
Intelligence-Led SOC: Aggregates and analyzes threat data from multiple sources, including external intelligence feeds, to enhance threat visibility.
In summary, an Intelligence-Led SOC is more proactive, leveraging advanced technologies and threat intelligence to anticipate threats, while a Traditional SOC is often more reactive, relying on manual processes and known threat detection methods.
Key Components
An intelligence-led Security Operations Center (SOC) is essential for effectively managing cybersecurity threats and enhancing an organization's security posture. The successful implementation of such a SOC involves several key components that work together cohesively.
Here some of the key components of an Intelligence-Led SOC:
Comprehensive Sensor Deployment: Ensure comprehensive visibility through strategically deployed sensors to detect a wide range of potential threats.
Threat Intelligence Integration: Utilize structured threat information (STIX/TAXII) to create indicators of compromise (IOCs) that inform intrusion detection systems (IDS) and firewalls.
Threat Data Collection: Gather detailed threat data from various sources, including open sources, dark web, and internal logs.
CTI Advisory: Focus on understanding adversary techniques, which are harder to change than tools or IOCs, for long-term defense planning.
Detection Engineering: Develop, test, and tune custom detection analytics to optimize precision and recall in threat detection.
Automation and AI/ML: Implement automation tools and AI/ML algorithms to streamline alert processing, reduce false positives, and enhance decision-making.
Proactive Threat Hunting: Engage in continuous threat hunting to identify potential threats before they materialize into incidents.
Collaboration and Information Sharing: Foster collaboration across teams and with external partners to share threat intelligence and best practices.
Key: Threat Intelligence Integration
Integrating threat intelligence (CTI) into SOC operations is KEY for informed decision-making. Threat intelligence encompasses the collection, analysis, and dissemination of information about existing and potential threats to an organization's IT assets. The strategic value of cyber threat intelligence cannot be overstated. According to S-RM's 2023 Cybersecurity Insights report, 46% of C-suite business leaders and senior IT professionals consider threat intelligence to provide a "high value for money" in terms of return on investment. This investment supports:
critical decision-making processes related to strategy development,
resource allocation,
and efficient incident response,
ensuring that organizations can effectively allocate their resources to areas of greatest risk.
In addition, by leveraging threat intelligence feeds, SOC teams can assess risks and prioritize protective actions effectively. This information aids in understanding the tactics, techniques, and procedures (TTPs) of threat actors, enabling SOCs to anticipate and respond to attacks more efficiently.
For a more detailed view on the CTI benefits, read my CTI posting.
Framework for Building an Intelligence-Led SOC
Building an effective, intelligence-led Security Operations Center (SOC) involves a systematic approach that integrates strategy, technology, and human resources. The framework focuses on establishing processes that leverage threat intelligence and automation to enhance the capabilities of security analysts, ultimately improving the organization’s ability to detect and respond to security incidents.
Step-by-Step Guide
Step 0: Assess Security Needs and Align with Business Goals
Clarify Business Objectives:
Determine why you need a SOC and align its goals with the organization's overall strategy.
Assess Current Security Posture:
Evaluate existing security measures and identify gaps that the SOC will address.
Step 1: Define Your Threat Model
To kick off the framework, organizations should define their threat model, which involves identifying and prioritizing the threats that are most relevant to their specific environment. Conducting a thorough threat assessment that considers industry standards, data assets, and current security posture is essential in this step.
Step 2: Establish an Intel-Driven SOC
An intelligent SOC goes beyond traditional operations by utilizing tools that incorporate threat-intelligence, artificial intelligence (AI), machine learning, and behavioral threat analysis. This enhances the ability of analysts to quickly identify and respond to threats. Integrating various threat intelligence feeds further improves the SOC's effectiveness.
Secure Network Architecture:
Establish a scalable and flexible network architecture that supports integration of various cybersecurity tools.
Data Integration:
Ensure seamless integration of telemetry from diverse sources (endpoints, networks, cloud services).
SIEM and Automation Tools:
Deploy Security Information and Event Management (SIEM) systems and automation tools to streamline processes.
AI/ML Integration:
Implement AI and ML solutions to enhance threat detection and response.
Threat Intelligence Platforms (TIPs):
Utilize CTI Advisory to:
Establish a robust cyber threat intelligence program tailored to your organization's specific risk profile.
Enhance situational awareness through regular briefings on relevant threats and emerging trends
Integrate threat intelligence into strategic decision-making processes and tactical security operations
Develop and implement proactive defense strategies based on actionable threat intelligence insights
Utilize TIPs to aggregate, analyze, and disseminate threat data.
STIX/TAXII Implementation:
Leverage STIX/TAXII for standardized threat information exchange.
Step 3: Embrace Automation
Automation plays a crucial role in reducing the manual workload on analysts. By streamlining repetitive tasks, organizations can alleviate alert fatigue and enable security teams to concentrate on higher-value activities such as threat hunting and incident response. Automating processes should be a priority to enhance overall efficiency.
Step 4: Optimize Tool Selection
When building a SOC, it is important to follow the principle of "deploy as few tools as possible but no fewer." This ensures that each selected tool serves a clear purpose, minimizing technical debt and the complexity of support. The right combination of tools can help eliminate redundancy and streamline operations.
Step 5: Continuous Improvement and Feedback
Establishing feedback mechanisms is vital for the ongoing evolution of the SOC. This includes regular assessments of current capabilities and the effectiveness of tools and processes. Continuous improvement allows the SOC to adapt to new threats and changing organizational needs.
Feedback Loops:
Establish processes for regular review and adjustment of automation strategies.
Stay Updated with Emerging Technologies:
Continuously integrate new technologies to enhance SOC capabilities.
Step 6: Staffing and Training
Identifying and retaining skilled personnel is critical to the success of an intelligence-led SOC. Organizations must invest in recruiting talent and providing ongoing training to ensure that team members remain adept at managing emerging cybersecurity threats. Employee retention strategies and fostering a positive work environment also contribute to the overall effectiveness of the SOC.
Recruit Skilled Professionals:
Hire analysts with expertise in threat intelligence, AI/ML, and cybersecurity operations.
Provide Continuous Training:
Ensure ongoing training and certification to keep up with evolving threats.
Let’s wrap it up…
An intelligence-led SOC, or threat-informed SOC, flips the script on traditional reactive security. Instead of simply responding to alerts, it uses threat intelligence to proactively hunt for and mitigate risks before they become breaches. Here's how it delivers a powerful advantage:
Proactive Threat Hunting: Instead of waiting for alerts, threat intelligence guides proactive hunts for malicious activity, allowing you to identify and neutralize threats lurking in your environment before they can detonate.
Prioritized Alert Triage: Drowning in alerts? Threat intelligence helps prioritize alerts based on actual risk, allowing your team to focus on the most critical threats and reduce alert fatigue.
Improved Detection and Response: By understanding the tactics, techniques, and procedures (TTPs) of relevant threat actors, your SOC can develop more effective detection rules and response playbooks.
Reduced Dwell Time: Early detection, powered by threat intelligence, significantly reduces the time attackers have within your network, minimizing potential damage.
Better Resource Allocation: Focus your resources where they matter most. Threat intelligence informs resource allocation, ensuring your security investments are aligned with the most relevant threats.
Enhanced Threat Visibility: Gain a deeper understanding of the threat landscape specific to your organization, enabling you to anticipate and prepare for emerging threats.
Strengthened Security Posture: By proactively addressing vulnerabilities and hunting for hidden threats, you bolster your overall security posture and reduce your attack surface.
Data-Driven Decision-Making: Threat intelligence provides data-driven insights that empower informed security decision-making, from incident response to long-term security strategy.
Stop playing catch-up with cybercriminals. The shift to an intelligence-led SOC isn't just a best practice—it's a necessity. Embrace proactive security, outsmart the adversaries, and safeguard your organization's future.
Ready to transform your security operations? Let's talk!